Don't Get Caught Off Guard: 5 New Cybersecurity Threats to Prepare For Now
The year 2023 marked a significant turning point for cyber-attacks with the introduction of AI (artificial intelligence), now in the hands of people...

1 in 4 businesses reported ransomware attacks on cloud data.
Every business is vulnerable to cybercriminals and hackers. Migrations to the cloud are moving faster than ever. Setting up your Microsoft 365 cloud service tools or Google Workspace with advanced security configurations will provide you with your basic office functionality as well as a safe place to store and share information.
This article outlines key configurations to increase the security of your organization.
Microsoft recommends that you review and complete the tasks listed here.
1. Set Up Multi-Factor Authentication
Using multi-factor authentication (MFA) is one of the easiest and most successful ways to increase the security of your organization. This can prevent hackers from taking over if they know your password.
Multi-factor authentication means you'll type a code from your phone to get access to Microsoft 365. Here's how to add two-step verification to your personal Microsoft account.
To set up multi-factor authentication in Microsoft 365, you turn on Security defaults:
You enable or disable security defaults from the Properties pane for Azure Active Directory (Azure AD) in the Azure portal.
Sign in to the Microsoft 365 admin center with global admin credentials.
In the left nav choose Show All and under Admin centers, choose Azure Active Directory.
In the Azure Active Directory admin center choose Azure Active Directory > Properties.
At the bottom of the page, choose Manage Security defaults.
Choose Yes to enable security defaults or No to disable security defaults, and then choose Save.
After you set up multi-factor authentication for your organization, your users will be required to set up two-step verification on their devices.
For full details and complete recommendations, go to set up multi-factor authentication for users.
2. Use Dedicated Admin Accounts
The administrative accounts you use to administer your Microsoft 365 environment include elevated privileges. These are valuable targets for hackers and cybercriminals. Use admin accounts only for administration.
Admins should have a separate user account for regular, non-administrative use and only use their administrative account when necessary, to complete a task associated with their job function. Also, ensure the admin accounts are set up for multi-factor authentication.
3. Raise the Level of Protection Against Malware in Mail
Microsoft 365 includes protection against malware. You can expand this protection by blocking attachments with file types that are commonly used for malware. To bump up malware protection in email:
Go to https://protection.office.com and sign in with your admin account credentials.
In the Security & Compliance Center, in the left navigation pane, under Threat management, choose Policy > Anti-Malware.
Double-click the default policy to edit this company-wide policy.
Select Settings.
Under Common Attachment Types Filter, select On. The file types that are blocked are listed in the window directly below this control. You can add or delete file types later if needed.
Select Save.
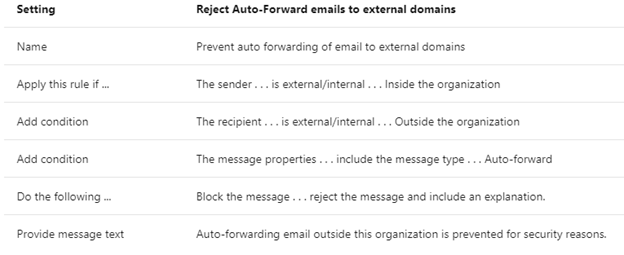
4. Stop Auto-forwarding for Email
Hackers who gain access to a user's mailbox can exfiltrate mail by configuring the mailbox to automatically forward email. This can happen even without the user's awareness. You can prevent this from happening by configuring a mail flow rule.
To create a mail transport rule:
Go to the Exchange admin center.
In the mail flow category, select rules.
Select +, and then Create a new rule.
Select More options at the bottom of the dialog box to see the full set of options.
Apply the settings in the following table. Leave the rest of the settings at the default, unless you want to change these.
Select Save.
5. Use Office Message Encryption
With Office Message Encryption, your organization can send and receive encrypted email messages between people inside and outside your organization and it’s compatible with Outlook, Yahoo!, Gmail, and other email services. Email message encryption helps ensure that only intended recipients can view the message content.
Your organization might have configured additional options that apply a label to an email, such as Confidential.
For more information, see send, view, and reply to encrypted messages in Outlook for PC.
Cloud data protection is a shared responsibility between Microsoft and the business entity.
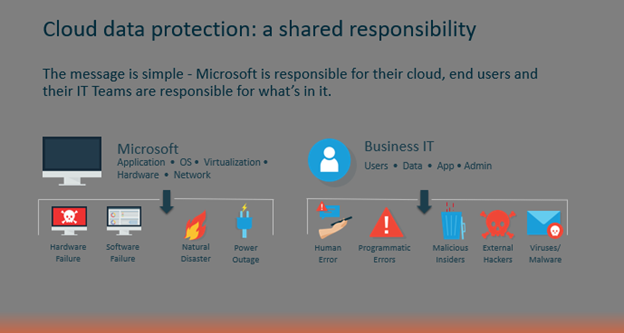
Microsoft works off what is called a shared responsibility model. The message is simple, Microsoft is responsible for their cloud, and end-users and the Businesses are responsible for what’s in it.
As you can see, the model has two sides. On one side is Microsoft, and on the other, the end-user and their business IT professional.
Microsoft takes full responsibility for its operating system... network applications, virtualization, and hardware. So, for example, in the case of a natural disaster or power outage resulting in cloud hardware or software failures, they’ve got your back. They're guaranteeing uptime and availability.
Protection of the data, and administration of the application, falls on end-users and the business.
Data being deleted or compromised due to basic human error, hackers, ransomware, or disgruntled employees on a deleting spree…all are highly impactful and are left to the end-user and the Business IT to have their own plan on how to recover.
Primarily because there is a common misconception that the “cloud” is impenetrable or bulletproof and that organizations such as Microsoft and Google just by the nature of their size and scope...they somehow have you and your data protected.
Unfortunately, that's not the case and both companies make this clear. Microsoft for example in their SLA specifically states that they're not liable for any type of data loss due to application outages, nor are they liable for data loss associated with deprovisioned accounts.
They go as far as recommending that you regularly back up your content and data that you're storing in their apps and services using a third-party application in Section 6 of their SLA.
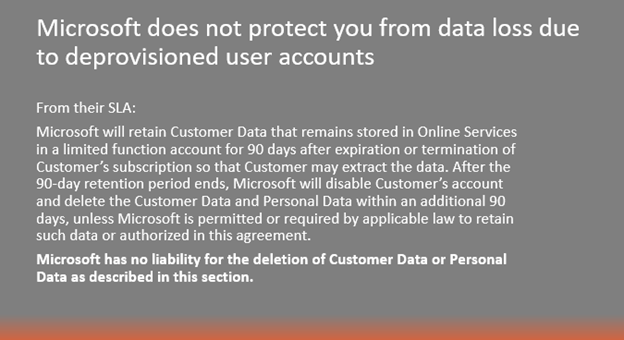
Essentially, if you put data in their cloud, it’s your problem if something goes wrong that’s not environmental. This is where most organizations start to feel the pain of not having a backup.
Nothing is stopping users from deleting data, changing data, or doing stupid things like clicking on Ransomware. And Microsoft has no responsibility to provide protection from these occurrences or help you with recovering.
Although Microsoft stores data in their servers, they don’t take responsibility for the data created by Microsoft 365 end users. An independent backup separated from the app itself is necessary to avoid the most common data loss pitfalls such as:
Without sufficient backup, businesses stand to risk losing all of their files. SaaS Protection serves as an insurance policy against Microsoft 365 outages, accidental deletion, and ransomware attacks, providing a secure second location to retrieve necessary data in as little as seconds.
For more information, please visit the following sites.
Microsoft 365:
Teknologize is a SOC 2 certified, Professional Technology Services company with clients throughout the Pacific Northwest. We have offices located in:
Questions about your IT or Cybersecurity? Give us a call today!

The year 2023 marked a significant turning point for cyber-attacks with the introduction of AI (artificial intelligence), now in the hands of people...

At Teknologize, we continually invest in security best practices to ensure that our client’s data stays safe and secure. As a part of an ongoing...

If you’re hoping to cut costs and boost profitability without compromising productivity or efficiency, assessing the technology you use in day-to-day...