Tax Season W-2 Scam: How Small Businesses Can Prevent Payroll Fraud
February has a rhythm every business owner knows. Your accountant is asking for documents.Your bookkeeper is reconciling numbers.Payroll is...
Hackers initiate 2,244 attacks per day. Every link clicked, email opened, app downloaded, and network joined is an opportunity for hackers to compromise your data. The days of just using firewalls or antivirus to catch and stop breaches are gone, and they have been gone for a long time.
Cybercrime is a trillion-dollar industry, and that’s all the motivation the bad guys need.
To ensure complete network security, more is needed than antivirus protection. Endpoint Security covers your entire network and protects against different types of security attacks, while antivirus software covers a single endpoint and only detects and blocks malicious known files.
Antivirus scans an operating system and file system for known “bad” files such as malware, trojans, worms, and ransomware, and upon detecting them, removes them from the system.
Traditional, reactive tools such as firewalls and antivirus software generally depend upon known threat information to detect attacks.
Most antivirus programs rely on a library or database of known viruses that they use to compare with programs on a user’s device. These threats are considered "known" threats.
The reality is that not all threats are known. To get past security products that successfully block known threats, attackers are forced to create something that has never been seen before, “unknown”. The internet is packed with a whole host of fast-evolving malware and other exploits that are unrecognized by and invisible to traditional antivirus software.
“Endpoint” refers to any device utilized by an end-user, in a corporate setting. These devices commonly include desktop PCs, workstations, tablets, smartphones, servers, printers and any other IoT devices that connect to the internet.
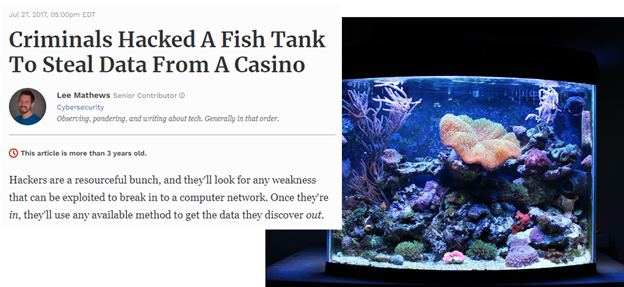
Hackers stole data from a Casino via the fish tank (endpoint) connected to their network.
Every endpoint in a network stands as a potential “entry point” for security threats. Therefore every device that is connected to the network carries the risk of becoming a cyber criminal’s entrance. Endpoints are always at constant risk of falling prey to malware.
Further, with trends like BYOD (Bring Your Own Device), these risks have become even more intense.
Endpoint Security, also known as Advanced Endpoint Protection and Endpoint Protection, aims to protect the IT infrastructure at large by protecting the endpoints as gateways to it.
Advanced Endpoint Protection extends beyond antivirus, including next-generation protection features like advanced persistent threat detection, investigation and response, device management, data leak prevention, and others, protecting systems from file, fileless, script-based, and zero-day threats by using machine-learning or behavioral analysis. Advanced Endpoint Protection guards a corporate network by blocking access attempts and other malicious activities at their endpoints.
Endpoint Protection provides safeguards against internal threats as well by allowing only certain devices to connect. An IT admin might let a USB mouse connect while disabling a USB hard drive. These settings prevent employees from stealing large amounts of valuable company data or delivering malware via a USB stick.
Antivirus and Endpoint Security protect your devices and data, but both are significantly different from each other.
1. Endpoint Security software designed for the organization's IT infrastructure as a whole.
Endpoint Security software is built exclusively with organizations in mind. As antivirus software deals with devices on an individual basis, threat-detection alerts will only be available on the device affected.
With Advanced Endpoint Protection, a system administrator can monitor devices, examine suspicious activities, manage updates and patches, and remotely solve device issues. Security software provides an administrator a portal through which security professionals can configure and monitor multiple company devices together.
This is not a standard among antivirus software products and resolves the issue of managing individual devices. Antivirus is operated as a single program, whereas Endpoint Security is often offered as a suite with the capability to integrate with third-party solutions.
2. Endpoint Security software protects against internal threats.
In 2020, 60% of data breaches were from insiders. (Source: ID Watchdog)
Most antivirus software does little, if anything, to protect your data from those who access it every day.
Endpoint Security provides a suite of tools to prevent data loss. These tools include data access protocols that ensure that only authorized employees access certain data. They also include measures to encrypt data.
3. Endpoint Security solutions are customizable.
System administrators can block certain applications and endpoints from connecting to the network. Security also includes web filtering allowing system administrators to block websites known to trick users into downloading malware or ransomware.
System administrators can also set up policies to manage which employees are able to access confidential information.
4. Endpoint Security protects against known AND unknown threats.
Antivirus software can identify known malware and threats, and detect and respond to known threats after they’ve entered your network.
With a massive increase in cybersecurity breaches and the ever-evolving threat landscape, preventive techniques used by Endpoint Security can protect your organizations against advanced threats including, zero-day threats, fileless and signatureless malware, phishing attacks, drive-by malware, and more.

Source: Ponemon Institute, sponsored by Morphisec
Advanced Endpoint Protection is a system of technologies that protect against all stages of an attack.
1. Prevention: Stopping malware before it can execute.
Prevention focuses on stopping malware from ever reaching the device in the first place. Prevention capabilities can be broken down into exposure prevention and pre-execution defense.
Exposure prevention:
Web protection – can you block malicious webpages?
Device control – which devices (e.g., USB drives) are allowed to access the endpoint?
Download reputation – where does the file come from, do other machines in the organization use it?
Pre-execution defense:
File analytics – does a file contain code trying to modify the registry?
Emulator – can you execute the file in a safe environment to test it?
2. Detection: Identifying quickly when malware is deployed.
Catching malware in the act.
Malicious traffic detection – are processes communicating with known threat locations, i.e., phoning home?
Memory scanning – is a file exhibiting behavior of known malware?
Exploit detection – is the suspect process cataloging the memory of another process?
3. Response: Taking action instantly when malware is detected.
Clean-up and analysis to identify the entry point of the malware.
Malware removal – can your endpoint solution remove the executable and other malware components?
Root cause analysis – can it identify the malware’s origin to understand what was compromised?
Antivirus just can’t keep up with modern cyber threats as they evolve and grow more malicious and frequent.
Unfortunately, simply having antivirus software isn’t enough to protect you anymore. In fact, nearly a year ago, security testing firm, SE Labs, indicated fewer than half of currently available antivirus programs were even sufficient at blocking known cybersecurity threats, let alone undiscovered, new, and advanced threats.
If you’re interested in learning more about Endpoint Security for your organization call 509-396-6640 or Contact us for more information!
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!

February has a rhythm every business owner knows. Your accountant is asking for documents.Your bookkeeper is reconciling numbers.Payroll is...
%20Enabling%20Secure%20Growth%20for%20Small%20Businesses.png)
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...