Endpoint Detection and Response (EDR): Enabling Secure Growth for Small Businesses
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

It’s a ransomware attack built for the cloud...
A ransomware attack is when an outside party accesses computer data and encrypts it or holds it hostage, demanding a ransom in order for the business or individual to regain access. Typically, the attacker will do this by sending a legitimate-looking email, also known as a phishing email, but when the unsuspecting person opens the email and clicks on a link, their data becomes encrypted.
It’s a ransomware attack built for the cloud that can infect and encrypt your hosted email as well as lock you out of OneDrive and SharePoint sites. In these attacks, the hacker uses phishing emails to gain control of the user’s email account. Once inside, the hacker can deploy ransomware that encrypts the victim’s email messages and can also cause additional damage by using the compromised email account to disperse more malware to the victim’s contacts.
Your business runs on email, so losing access to how you connect with customers, vendors, and the rest of your organization could be crippling.
These attacks can happen to anyone, and they're so sneaky that all it takes is one person clicking a wrong email to lock an entire business's files. As hackers continue to advance their approach, we'll start to see new strains build out this new category of ransomware.
This threat is demonstrated in the video below by Kevin Mitnick, formerly the most wanted hacker in the US now turned cybersecurity consultant.
In this sequence of images, Kevin Mitnick shows just how easy it is for your Office 365 emails to be infected by RansomCloud.
1. A phishing email hits your inbox. It looks like a pretty legit email from Microsoft and their AntiSpam Pro service. Let's open it up (click #1)
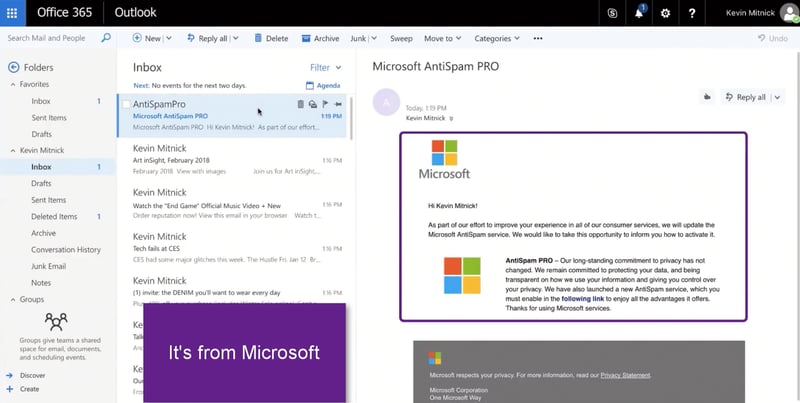
Phishing RansomCloud Exploit Hitting Inbox - Image Courtesy Datto
2. Briefly scanning the email, looks like there's an update to their AntiSpam service that you can enable by clicking the link. (click #2)
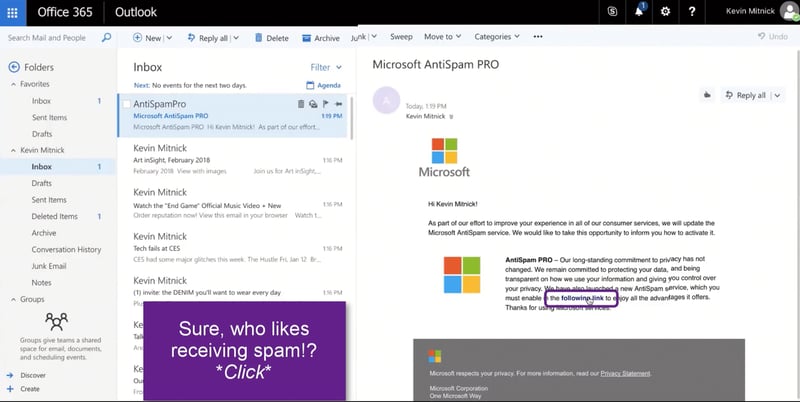
Phishing RansomCloud Request with Link - Image Courtesy Datto
3. This then prompts you to log into your Microsoft account.
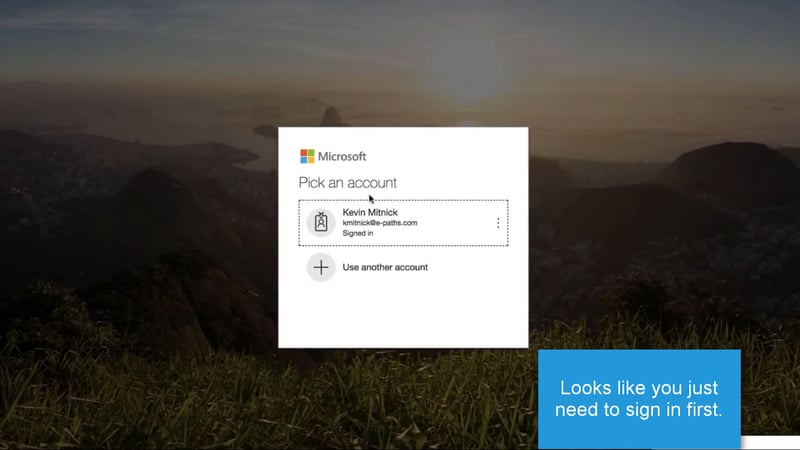
Phishing RansomCloud Log In Prompt - Image Courtesy Datto
4. You then grant permission to access your email.
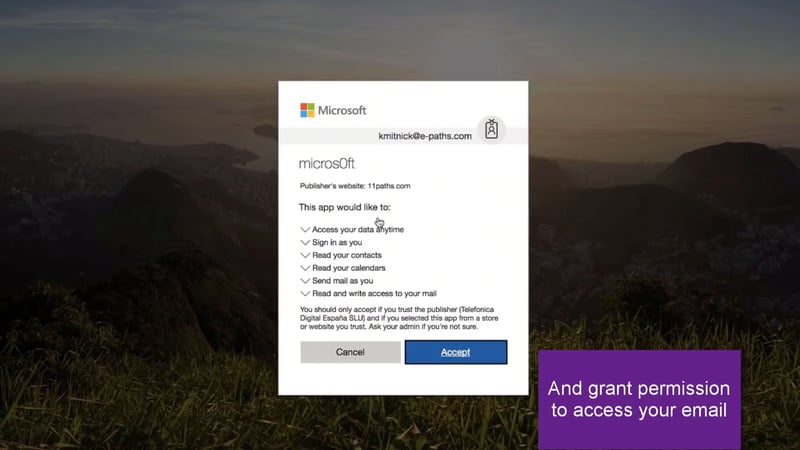
Phishing RansomCloud Granting Access to Email - Image Courtesy Datto
5. You're redirected back to your inbox. Everything looks fine, all emails are there...
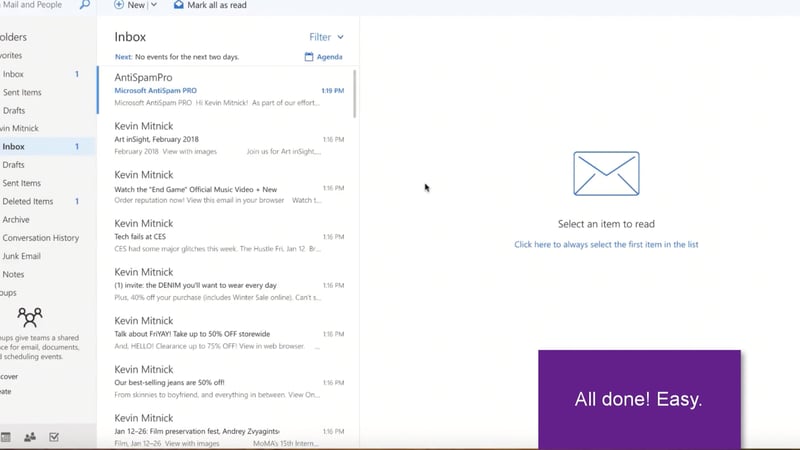
Phishing RansomCloud Inbox Before Encryption - Image Courtesy Datto
6. And then you find your entire inbox is encrypted because you fell for the phishing email that handed over access to your Office 365 inbox.
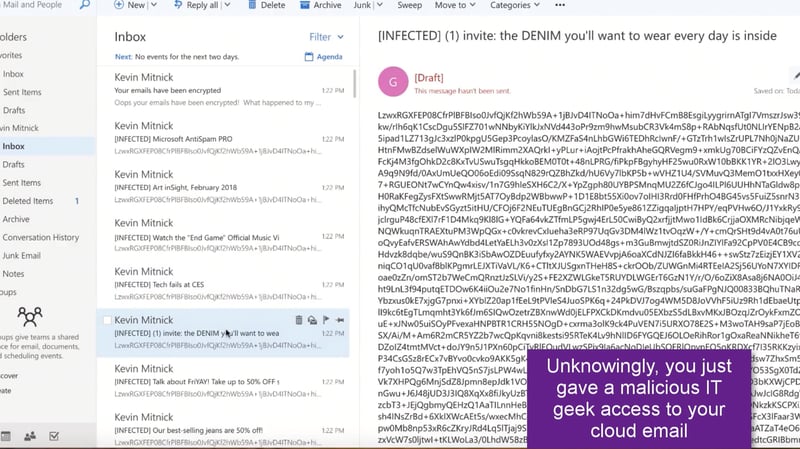
Phishing RansomCloud Encrypted Inbox - Image Courtesy Datto
7. Just like that, you're prompted to pay a ransom to decrypt and recover your emails.
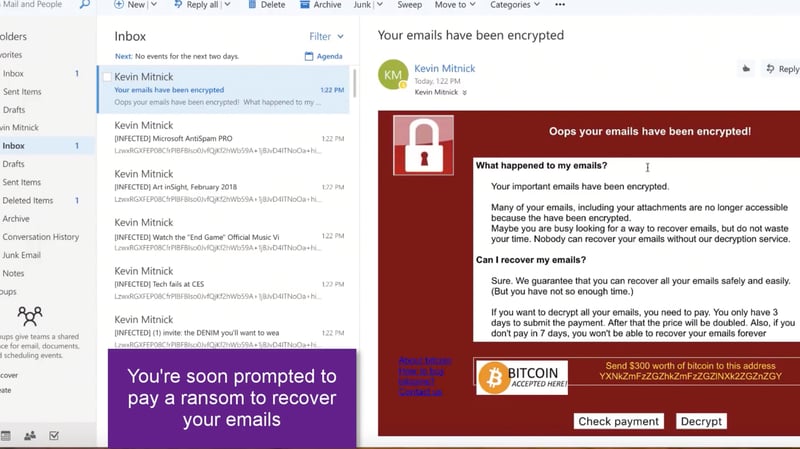
Phishing RansomCloud Pay to Decrypt - Image Courtesy Datto
Not commonly known is that Microsoft and Google don't back-up your files for you, and your traditional back-up works solely on your physical hardware, not what you have located in the cloud. To get complete back-ups of your cloud email and files you need to upgrade services with Microsoft, but industry experts recommend using a third party outside of Microsoft or Googles systems to back-up your data. If you do get RansomCloud and have third party back-ups, you can get back on your feet in no time.
As the cyber threat landscape continues to change as our technology does, be sure to change with it through cybersecurity services that look out for you.
Teknologize has clients throughout the Pacific Northwest with offices located in the Tri-Cities, Washington 509.396.6640 and Bend, Oregon 541.848.6072.
%20Enabling%20Secure%20Growth%20for%20Small%20Businesses.png)
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...