Endpoint Detection and Response (EDR): Enabling Secure Growth for Small Businesses
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

A SOC 2 audit isn’t just a one-time exercise. The audit must be completed yearly, inspecting performance and compliance over the last 12 months. Consistently completing a SOC 2 audit builds continuity of vital controls and processes.
Teknologize is committed to doing our part to protect our clients. Obtaining our SOC 2 Attestation through a third-party auditor allows us to continue to grow and operate at a more mature and secure level of compliance and security.
“SOC 2 compliance demonstrates to customers, clients, and security vendors that we have taken the necessary steps to protect data and systems from potential threats and breaches. Teknologize is committed to completing the SOC 2 readiness and audit process annually. We believe our commitment to data management and security best practices allows us to implement the same processes and controls for our clients."
Byron Martin, Teknologize CEO
A SOC 2 compliance audit measures an IT provider's network and system management services and their commitment to data management and security best practices. Therefore, the SOC 2 audit process and report allows businesses to assess and validate the integrity of the IT Provider they are trusting with their business and critical data.
Request a copy of the IT Provider’s SOC 2 report. The report is an attestation by a third party, allowing business leaders to trust the credibility of the assessment and have the reassurance that the IT Provider is implementing the necessary data governance, controls, and IT security required to protect your business. You’re not stuck relying on the IT provider’s “promise”.
If an IT Provider cannot complete a SOC 2 audit, they likely are not strictly implementing the data governance policies and procedures to protect your business.
A SOC 2 report can provide organizations with the assurance that their IT provider's systems and processes meet regulatory requirements, such as those related to data privacy and security.
Their best practices, security controls, and processes will ultimately help manage your business to appropriately store, manage and protect the critical data and systems relevant to your business.
Additionally, a SOC 2 report empowers decision-makers to eliminate those providers who may put their business data and reputation at risk.
This helps organizations make informed decisions about the providers they choose to work with and ensure that they are entrusting their sensitive data to IT Providers that have demonstrated a commitment to protecting that data.
Furthermore, it can also give you an idea about the level of security and compliance that the provider maintains, which can be useful if your company is required to comply with certain regulations or industry standards.
Many IT providers are not willing to invest in the SOC 2 attestation process.
Why?
It takes a significant commitment of money, time, and company resources to complete the audit process.
The audit also enforces IT Providers to hold their own organization accountable by noting any gaps in their efforts to safeguard both internal and client-related data.
.png?width=500&height=250&name=SOC%202%20TYPE%201%20COMPLIANT%20(1).png)
By using an IT Provider that is SOC 2 compliant, your vendors, customers, and clients can be assured that you’re following the necessary controls and best practices to protect their critical data and information.
SOC 2, Service Organization Control, is a set of security standards developed by the American Institute of Certified Public Accountants (AICPA) designed to ensure that service organizations have adequate controls in place to protect the security, availability, processing integrity, confidentiality, and privacy of the customer's data.
SOC 2 reports, which are issued by independent auditing firms, provide assurance that an organization's controls and processes related to security, availability, processing integrity, confidentiality, and privacy meet a set of specified criteria.
SOC 2 is widely recognized in the technology industry as a standard for ensuring the security and reliability of cloud-based systems.
SOC 2 is important for a number of reasons.
A SOC 2 report measures the controls of a service organization related to the five "trust services criteria" outlined in the SOC 2 framework:
The SOC 2 report includes a description of the service organization's controls, as well as an assessment of the effectiveness of those controls, over a specific period of time. It is based on an evaluation of the service organization's controls by an independent, third-party auditor.
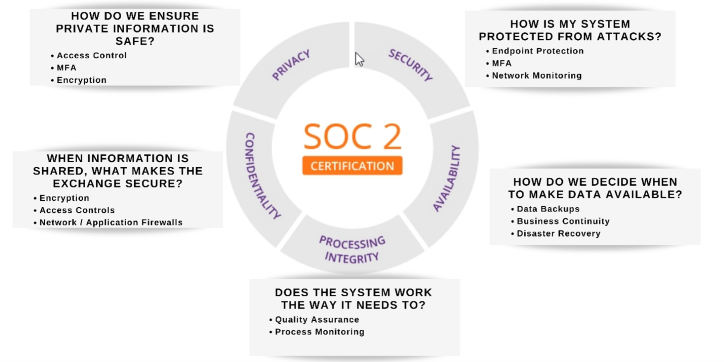
It is important for an IT provider to have a SOC 2 attestation because it shows that the provider has undergone an independent, third-party assessment of its controls and has demonstrated that it meets the relevant standards. This can help customers feel more confident in the security and privacy of their data when using the provider's services. It can also help the provider to stand out in a crowded market and win new business.
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!
%20Enabling%20Secure%20Growth%20for%20Small%20Businesses.png)
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...