Why Low-Cost IT Support Costs More | True MSP vs. Fake MSP
IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...

The FBI defines Business Email Compromise (BEC) as “a sophisticated scam that targets both businesses and individuals who perform valid transfer-of-funds requests. The scam is carried out by compromising legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.”
Business email compromise (BEC), is also referred to as CEO fraud and funds transfer fraud.
We see two main scenarios when it comes to Business Email Compromise, BEC.
Impersonating the CEO or other key employees with a fake but similar email address.
Cybercriminals impersonate the company CEO or other company executives with a spoofed email domain, asking employees, typically in HR or accounting to help them out by sending a wire transfer. They are betting that most people don’t look at email addresses very closely or that they’ll notice minor differences in spelling.
Using social engineering techniques that rely on winning the trust of the email recipient, these emails use familiar yet urgent language and make it clear that the recipient is doing the sender a big favor by helping them out. Cybercriminals prey on the human instinct to trust one another and on the desire to want to help others.
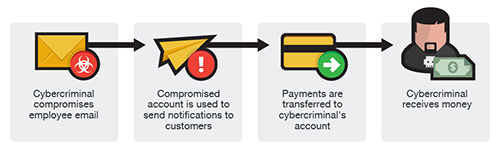
Company Email has been hacked and the cybercriminal is impersonating key roles using the real email.
Cybercriminals have breached your company email possibly through a malware attack, or through phishing scams. Then they take their time, research key personnel within the business as well as figure out who your paying vendors or clients are. Using your valid company email, they send payment requests or invoices with payment instructions to an account they control.
Every organization should assume they will be targeted by a BEC attack.
Spear phishing emails are the most popular targeted attack vector
Symanetc’s Internet Security Threat Report 2019 shows spear phishing emails are used by almost two-thirds (65 percent) of all known groups carrying out targeted cyberattacks. The report also tells us that 96 percent of targeted attacks are carried out for the purpose of intelligence gathering.
The Bogus Invoice
This scam involves targeting businesses that have an established relationship with a supplier. An email account of an employee is hacked, usually someone in the billing or finance department, and then used to make requests for invoice payments to an alternate fraudulent account controlled by the hacker. Emails are sent to multiple vendors identified from the employee’s contact list. The business may not become aware of the scheme until their vendors follow up to check the status of the invoice payment.
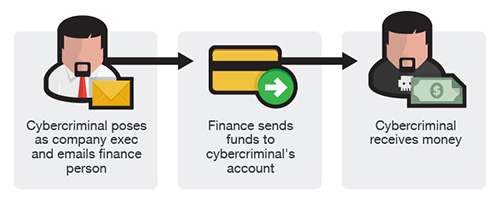
CEO Fraud
In this version, the fraudsters identify themselves as high-level executives (CFO, CEO, CTO, etc.), lawyers, or other types of legal representatives and claim to be handling confidential or time-sensitive matters that require a wire transfer to an account they control.
Should a CEO fraud incident take place, there are immediate steps to take:
Contact your financial institution immediately.
Notify your attorneys.
Contact law enforcement.
File a complaint with the FBI’s Internet Crime Complaint Center (IC3).
Brief senior management.
Conduct IT forensics for a full investigation of the attack.
Contact your insurance company.
Consult with outside security specialists.
Isolate security policy violations.
Draw up a plan to alleviate security weaknesses.
Click here to download the full 10-step CEO Fraud Response Checklist!
The typical first response toward risk mitigation focuses on technology. But in addition to technical safeguards, we must take into consideration the human element also known as the human firewall. Security awareness training plays an essential role in creating a human firewall around your organization.
When users are trained and aware of the different aspects of phishing attacks, this arms them with the ability to recognize and avoid even the most sophisticated attempts of Business Email Compromise.
Cybercriminals know that employees are the weakest link in any organization’s IT system. Therefore, they continue to rely on phishing and other social engineering tricks. Establishing a human firewall won’t eliminate breaches entirely, but it will reduce them.
The following is a minimum of what to have in place to protect yourself:
Technology
The Human Firewall
CEO fraud isn’t going away. As cybercriminals become smarter and use social engineering to spoof emails, employees in every organization must be aware of the dangers.
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!

IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

“When did this happen?”“About a year ago… well, thirteen months, actually.”