Endpoint Detection and Response (EDR): Enabling Secure Growth for Small Businesses
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...
According to Help Net Security, 90% of successful cyberattacks occur through email-based attacks.
Additionally, 1 out of every 8 employees shares the information requested in phishing emails.
Email is a Love Hate Relationship
Email is critical. It is the most used internet-enabled service for businesses. It is the core of professional and personal lives.
Email is a massive hassle. It is filled with spam, phishing emails, malware, and ransomware. Plus, a growing number of highly sophisticated spear phishing attempts can cause massive financial and personal harm to your business.
Emails are the most common path of cyberattacks. In a typical scenario of a successful attack, as an example, an employee of a company receives a phishing email and opens it. The link or the attachment consists of malware that spreads through the system granting the attacker access to your network now exposing the entire company to the threat of leakage of highly confidential data, including your client or patient data.
Most of the popular email platforms have basic filtering capabilities, but these are no longer enough.

Spam Email
More than half of all email messages in the world are spam. Spam emails are typically emails trying to sell you a product or persuade you into taking some type of action like donating to a cause.
Graymail
Graymail isn’t quite spam. The email recipient did opt-in to receive it at some point. For instance, when a consumer is checking out at an online retail store and provides their email address for order confirmation and updates. Moving forward the consumer receives sales emails on a regular basis.
Phishing and Spear Phishing
Phishing emails pose more of a danger as they seek to steal your personal or company information for malicious purposes. Once personal information such as account logins or credit card information is taken, your personal accounts can be hacked, or you can become a victim of financial fraud.
Phishing is the method of attempting to get personal and sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy party such as popular shopping, social, and banking/financial sites. Phishing is one of the easiest forms of cyberattacks to execute, and it’s also one of the easiest to fall for.
Spear phishing aims at specific employees of an organization with many goals, such as gaining unauthorized access to networks, data and applications or diverting a wire transfer into the cybercriminal's account. In contrast to the rapid, mass email approach of phishing, spear phishing is methodical, deliberate, and narrowly focused. They do their research.
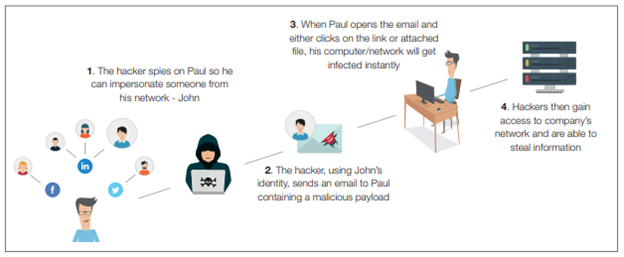
Image courtesy of VadeSecure - The progression of a spear phishing attack
Spear phishing emails are essentially invisible to standard spam email filters. Spam filters look for URLs, topics, and keywords that signal that something isn’t right about the message. The filter is trained to look for phrases like “Easy Ways to Save on Your Auto Insurance”. Not “Hey, Jon. It’s Mike. Give me a call.”
There is no URL in the message that could get flagged. There is no file attachment and there is no suspicious keyword or phrase. The message breezes through to the inbox and the potential for malware or wire fraud happening now increases. The phishing or spear phishing email is simply the point of entry into the network.
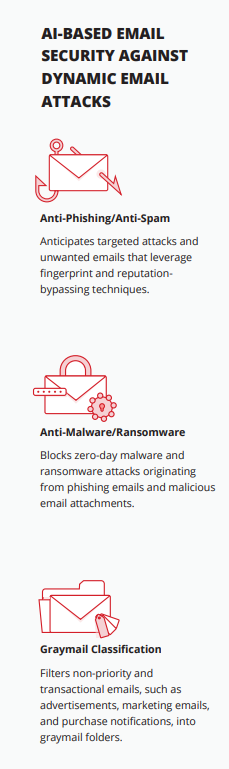
There are advanced programs available that can be used to monitor and flag phishing emails. Using AI and behavior monitoring to find more threats, versus only matching to known documented email threats. These filters add an extra layer to your email security than just having the standard spam filters enabled.
Sophisticated email filters use artificial intelligence, AI, to monitor hundreds of millions of email boxes looking for phishing threats. It evaluates email content, requests for credentials, phone numbers, any linked website content, and images including QR codes, text-based images, and brand logos.
Every URL that is included in any email is checked to see if it contains any malware or other malicious code and is done at the time an employee clicks on it. Some filtering solutions examine URLs at the time the email is received by the network. Sophisticated hackers will now send emails that include URLs that initially lead to innocent websites, then wait to redirect those URLs an hour or two later, thus bypassing most filtering systems unless the site is examined at the time of click.
Attachments are analyzed, scanning for malicious links and examining code in attachments such as PDFs, Word documents, and archive files.
What about spam emails with fraudulent domains? The spoofing protection in the software identifies every incoming email that attempts to spoof trusted company domain names, display names, and even similar but different email addresses that are close to real ones. It looks to identify similarities between new senders and all your previous contacts to detect if there is a spoofing attempt targeting your company even highly sophisticated one-off spear-phishing attempts.
Lastly, you can include educational banners for users who receive phishing emails informing them of the threat posed and how they can avoid it. These impossible to ignore integrated banners alert users to the possibility of a phishing attempt right in the message itself. The software will also alert IT administrators if users have ignored phishing warnings on either email links or URLs and have thereby potentially created a breach of security.
Spam email filters should be a piece of your cybersecurity infrastructure. Protect your business email from advanced email security threats, including phishing, spear phishing, and malware. Keep in mind that the more layers of security you add mean more barriers between your network and a hacker.
Let us know how we can help you strengthen your email security!
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!
%20Enabling%20Secure%20Growth%20for%20Small%20Businesses.png)
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...