How to Build a Strategic IT Budget for Your SMB | Teknologize
Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

Phishing/social engineering is the #1 cause of data breaches and the primary delivery method for ransomware.
While amateur phishing emails are easy to block, spear phishing attacks are becoming more sophisticated and harder to detect.
A highly targeted form of phishing, spear phishing involves tailored emails being sent to well-researched victims while pretending to be a trusted sender.
The most common goals of spear phishing attacks include:

These attacks are personalized and may refer to their targets by their specific name or job position. Attackers invest time in researching their targets and their organizations to craft a personalized message, often impersonating a trusted entity.
Here are 7 reasons why spear phishing attacks are so successful:
1. Spear Phishing Messages Target Their Victims
These messages are designed to look like they are sent by a manager or high-level executive. They also can be customized to look like they come from a trusted vendor that your company works with regularly.
2. Each Spear Phishing Email Looks Authentic
Hackers spend a lot of time and effort planning their spear phishing attacks. They design their fake emails to look as authentic as possible to trick recipients into thinking they are from a legitimate source.
This means using spoofed email addresses, business logos, design, and language that can pass as legitimate. Because they don’t share a lot of the similarities of traditional phishing emails, these messages are often missed by spam filters.
3. Businesses May Be Lacking Security Tools
Many companies don’t have their cybersecurity hygiene – security patching, email filters, firewalls, and anti-virus— current and up to date. This leaves businesses vulnerable to all types of threats, including spear phishing attacks.
4. Spear Phishing Attacks Happen Over Time
Spear phishers are patient with their targeted phishing attacks. They often use multi-stage attacks that involve malware downloads and data exfiltration which can be set up over weeks or even months.
According to CSO, spear phishing attacks can be broken down into three main steps:
5. Employees Are Uneducated about What to Look for in a Phishing Email
Companies must trust the safety and security of their business and customers to employees who may not know how to recognize a targeted phishing attack. The point of security awareness training is to educate employees on what is considered risky, what clues to look for that indicate a threat, and how to respond.
6. Spear Phishing Leverages Zero-Day Exploits
Zero-day vulnerabilities are unknown software flaws in browsers, desktop applications, and plug-ins. Until they are fixed and patched, they can be exploited by attackers to compromise systems and gain access to the network and other resources, including personal and financial data.
7. Not all Businesses Use Spam Email Filtering Designed for Phishing and Spear Phishing
There are advanced spam email filtering programs available that can be used to monitor and flag phishing emails. Using AI and behavior monitoring to find more threats, versus only matching to known documented email threats. These filters add an extra layer to your email security than just having the standard spam filters enabled.
According to a survey from The Ponemon Institute, “80% of respondents are very concerned about the state of their companies’ ability to reduce email-based threats, but only 29% of respondents are taking significant steps to prevent phishing attacks and email impersonation.”
To trick recipients into thinking they are reading an email from a trusted sender, spear phishers use a technique called “spoofing” that allows them to impersonate a legitimate sender and email address.
There are three primary methods of email spoofing:
Display Name Spoofing: Display name spoofing impersonates the email’s display name but not the email address making the message look like it comes from a trusted source. It’s effective because many email clients, especially on mobile, show only the sender’s name but not the email address.
Domain Spoofing: With domain spoofing, a spear phisher appears to use a company's domain to impersonate a company or one of its employees. When an email address is an exact replica of a trusted sender, users are unlikely to recognize that the email is spoofed.
Cousin Domain: A cousin domain, which is also referred to as a look-alike domain is an email address that is nearly identical to a legitimate one, with only a slight modification. In the past, cousin domain spoofing attempts were more obvious, such as mIcrosoft.com instead of microsoft.com. Today, attempts are more advanced and difficult to spot, such as employee@mybusinessnameltd.com instead of employee@mybusinessname.com. These subtle changes can be extremely difficult to spot for busy staff who quickly read and respond to emails, especially when they are urgent.
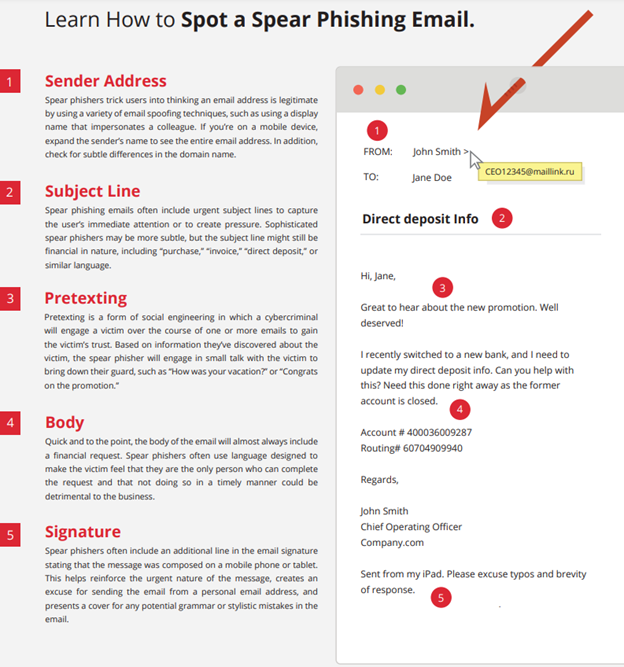
Image Courtesy of VadeSecure
Spam email filters should be a piece of your cybersecurity infrastructure. Protect your business email from advanced email security threats, including phishing, spear phishing, and malware. Keep in mind that the more layers of security you add mean more barriers between your network and a hacker.
When in doubt, check it out.
If you receive a message that you think is spear phishing, we recommend notifying your Managed Service Provider or IT admin for further investigation.
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

“When did this happen?”“About a year ago… well, thirteen months, actually.”

Artificial intelligence is everywhere, helping small businesses automate workflows, streamline processes, and boost productivity. But here’s the flip...