How to Build a Strategic IT Budget for Your SMB | Teknologize
Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

In a joint alert, Wednesday October 28th, 2020 from the FBI, DHS, and the Cybersecurity and Infrastructure Security Agency states “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers”. Key findings claim that Cybercriminals are targeting Healthcare and Public Health Sector with Trickbot malware, leading to Ryuk Ransomware attacks and ultimately data theft.
A new wave of coordinated attacks on US Medical facilities is already underway. Several hospitals in New York and Oregon have already been hit. Historically these attacks will target larger institutions first, then work their way to smaller medical centers.
KrebsonSecurity reported they began following a tip from a reliable source that a Russian cybercriminal group, known for deploying ransomware, was preparing an attack on more than 400 hospitals, clinics and medical facilities across the US.
The three federal agencies do not recommend that victims pay the ransom because there is no guarantee that files will be recovered and paying may encourage others to carry out cyberattacks.
90% of healthcare organizations experienced email borne attacks in the past year, with 25% suffering from very or extremely disruptive attacks.
Malware is short for malicious software. Malware typically consists of code developed by cyber attackers, designed to cause extensive damage to data and systems or to gain unauthorized access to a network.
Trickbot appeared in 2016 as a banking trojan malware which then evolved into a multi-use malware downloader that infects systems that are sold on to other criminal groups as a service. Trickbot steals sensitive information such as credentials, email, and point-of-sale data. It also downloads Ryuk ransomware which encrypts the system/network and ransoms the data for payment.
With Trickbot, the malware is typically embedded in an email designed to fool the recipient into clicking on a link or document that then installs the malware. Trickbot is the malware to gain access to the system. Ryuk is the ransomware that encrypts and exfiltrates the data to the hacker’s servers.
Small hospitals and healthcare centers are prime ransomware attack targets, as hackers see an increased likelihood these providers will pay the ransom demand because their services are critical as well as to prevent patient care disruption.
Researchers at the security firm Check Point said its survey showed health care has been the most targeted industry by ransomware in the US in October of 2020, with a 71 percent jump in attacks on US providers in October.
At least six hospitals were hit last week with cyber attacks.
St. Lawrence Health System in New York and Sky Lakes Medical Center in Oregon. 3 hospitals in New York and a medical center in Klamath Falls, Oregon had their systems compromised and brought down by ransomware attacks.
Headline courtesy of Healthcare IT News
Universal Health Services. In September 2020, UHS was hit with ransomware that took down its network that supports hundreds of healthcare facilities and hospitals.
UHS operates over 400 healthcare facilities in the US and the UK, has more than 90,000 employees and provides healthcare services to approximately 3.5 million patients each year.
Headline courtesy of Security Affairs
University Hospital in New Jersey. The hospital agreed to pay a ransom of $672,744, approximately 61.90 bitcoins on September 19th, 2020, to save 240 GB of stolen data.
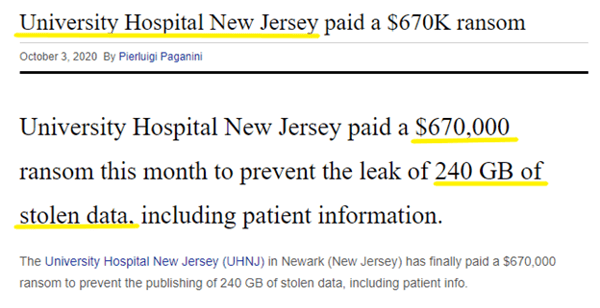 Headline courtesy of Security Affairs
Headline courtesy of Security Affairs
Duesseldorf University Hospital in Germany. Hackers disabled computer systems at Düsseldorf University Hospital in Germany and a patient died while doctors attempted to transfer her to another hospital roughly 19 miles away.
Headline courtesy of Verdict
Utah Pathology Services. 112,000 patients had their personal information exposed by a data breach.
Headline courtesy of KUTV, Utah
To get a more complete idea of what you can do to protect yourself download 15 Ways to Protect your Business from Ransomware.
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

“When did this happen?”“About a year ago… well, thirteen months, actually.”

Artificial intelligence is everywhere, helping small businesses automate workflows, streamline processes, and boost productivity. But here’s the flip...