How to Build a Strategic IT Budget for Your SMB | Teknologize
Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

Let’s face it, our world is filled with regularly occurring data breaches and cybersecurity events. Organizations need assurances that the companies they work with are doing everything they can to avoid exposing sensitive information and creating risk.
This is exactly what SOC 2 does.
SOC 2 Certification is vital because it holds businesses to a standard that protects customer data and privacy. It allows the consumer to have peace of mind knowing that a company is vetted, approved, and certified with one report. Going through a SOC 2 assessment requires the involvement of third-party auditors to prove that your organization meets the compliance requirements.
Achieving SOC 2 compliance offers many benefits, and confirms security protocols to protect sensitive information while following industry best practices.
With so much at stake, many businesses are only looking to partner with vendors that have implemented appropriate measures for preventing data breaches. Achieving SOC 2 certification proves the organization you’re partnering with has established practices with required levels of security across their organization to protect data.
Here are some benefits:
Improve your security posture and show your commitment to security and privacy.
Provides assurance to your customers and partners that your systems are secure with one report.
Satisfies requirements for regulatory compliance and corporate governance.
Builds good credibility and boosts brand reputation in the market.
Protects sensitive information stored in the cloud.
Accelerate the customer onboarding and due diligence process again with one report, eliminating vendor security questionnaires.
.png?width=400&name=SOC%202%20TYPE%201%20COMPLIANT%20(1).png)
SOC stands for System and Organizational Controls, developed by the American Institute of CPAs (AICPA), for the purpose of providing annual verification of the controls that a company has implemented to mitigate security and privacy risk.
Through a cybersecurity auditing process, organizations show the policies, procedures, and systems in place to prove they take cybersecurity and privacy seriously.
In a SOC 2 audit, an organization must provide information under the five categories called Trust Service Criteria which include:
Security (required)
Availability
Processing Integrity
Confidentiality
Privacy
The Trust Service Criteria includes security on organizational controls, access controls, basic risk assessment, as well as the ability to demonstrate change management.
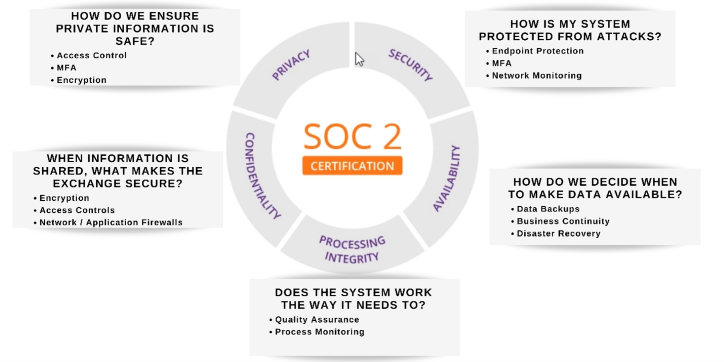
Security
The security criteria are all about protecting systems and information from unauthorized access and are required for all SOC 2 audits.
For data, it applies to collection or creation, ongoing usage and management, sharing, and storage. For the systems, this includes any systems that use electronic data. IT security tools such as endpoint protection, multi-factor authentication, and network monitoring are useful in preventing security breaches that can lead to unauthorized access of systems and data.
Availability
The availability criteria determines whether your employees and clients can rely on your systems to do their work.
Availability addresses whether systems have controls to support and maintain system operation, such as data backups, business continuity planning, and disaster recovery. Systems, products, or services are accessible for operation as specified by a contract or service level agreement (SLA).
Processing Integrity
The Processing Integrity Criteria determine whether a system works properly. Does it perform its intended functions without delay, error, omission, or accidental manipulation?
Examples include software development lifecycle management and quality assurance.
Confidentiality
The confidentiality criteria evaluates how organizations protect confidential information by limiting its access, storage, and use.
Confidential information may include personal information, as well as other information, such as trade secrets and intellectual property. This includes protecting confidential information throughout its lifecycle from collection and processing to disposal. Controls for confidentiality include encryption and identity and access management.
Privacy
The privacy criteria evaluates how organizations protect sensitive personal information, especially that which you capture from customers.
It’s similar to the confidentiality criteria but specific to Personally Identifiable Information, (PII).
Controls for privacy include privacy policies and consent management.
SOC 2 certification proves your organization has airtight internal security controls. It also builds trust with your customers. Your clients need to know that you’ll keep their data safe.
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

“When did this happen?”“About a year ago… well, thirteen months, actually.”

Artificial intelligence is everywhere, helping small businesses automate workflows, streamline processes, and boost productivity. But here’s the flip...