Endpoint Detection and Response (EDR): Enabling Secure Growth for Small Businesses
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

It’s a common misconception that ransomware attacks target only big businesses when in reality they target organizations of all shapes and sizes. Often going after the small to mid-range business as they don’t have the same budgets or IT personnel to invest in cybersecurity.
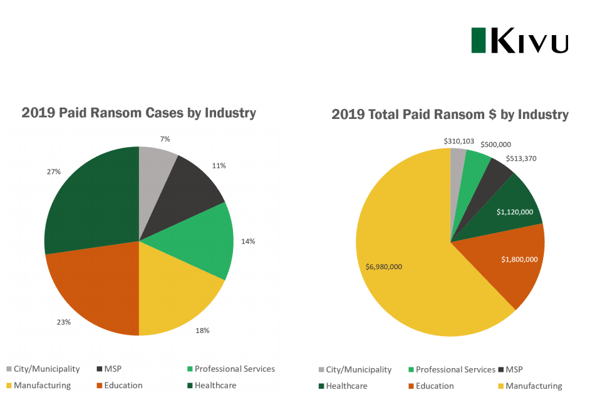
Picture Paid Ransomware cases
Image courtesy of Kivu Consulting
Part of Kivu’s paid ransom report shows that although manufacturing represented only 18% of the cases, manufacturing paid out 62% of the total sum of all ransom paid between all cases analyzed. The highest paid ransom at almost $2m! 67% of paid ransomware attacks against manufacturing came from a single variant the Ryuk crypto-ransomware.
Average cost to a ransomware attack image - The State of Ransomware 2020 - Sophos
Better to know your risks and vulnerabilities than to assume everything is OK. Reach Out for a FREE Vulnerability evaluation and we can help assess where you are at and help you build a roadmap for managing modern cyber risks.
Teknologize has clients throughout the Pacific Northwest with offices located in the Tri-Cities, Washington 509.396.6640 and Bend, Oregon 541.848.6072.
%20Enabling%20Secure%20Growth%20for%20Small%20Businesses.png)
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...