How to Build a Strategic IT Budget for Your SMB | Teknologize
Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

60 percent of small businesses that are victims of a cyber-attack go out of business within six months.
With the continued threat of cybercrime, it is clear there needs to be a focus in planning and conversation if any real improvements are to be made. But what questions should you be asking?
For some small- to medium-sized businesses (SMBs), allocating budget towards cybersecurity is a challenge. Unfortunately, these businesses are those that are most likely to be targeted for cybercrime. In fact, 43 percent of cyberattacks target small businesses.
Criminals know larger corporations have strong security systems, but smaller businesses frequently leave themselves vulnerable. If cybersecurity is not yet a priority for your SMB, it's time to change that. Luckily, there are things you can do to protect yourself, even when resources are limited.
1. Are your employees being appropriately trained on cybersecurity?
Security awareness training is essential for all businesses and organizations. The two primary threats, wire transfer fraud also known as Business Email Compromise (BEC), and ransomware depend on mistakes by employees to be successful. Wire transfer fraud tricks employees into transferring money to a fraudulent bank account instead of the intended recipients.
Ransomware is most often distributed by a phishing email attack and requires employees to open infected attachments or click on malicious links. Even well-configured systems with monitoring systems in place can let these emails slip by. The final and most important line of defense against these attack vectors is the person sitting at their computer deciding if what they are looking at is a legit email and not a phishing email.
All organizations should be providing mandatory security awareness training regularly to keep security at the top of everyone’s minds.
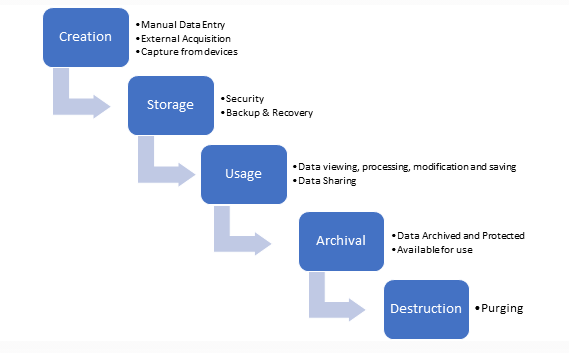
2. Do you know where your data is and how it is protected (data lifecycle management)?
Data life cycle management is a policy-based approach to managing the flow of an information system's data throughout its life cycle: from creation and initial storage to the time when it becomes archived or deleted. An information security program is concerned with the confidentiality and availability of your company data and the resources that access, store, and share that data.
Knowing how sensitive your data is in terms of compliance obligations, where it’s kept, where it is communicated, where it is used, who has access to it, and how long it should be kept is critical. For many organizations that data is core to their business. Very often this starts with classifying the data and establishing rules for the various classifications.
3. Can we detect an attempted or successful cybersecurity incident/breach?
An established cybersecurity program not only puts controls in place to prevent a cyber incident or breach, but also includes automated mechanisms to monitor their networks, systems, services, and users to notify them when something bad or unintended is happening.
Managed Detection and Response (MDR) purpose is to help companies and organizations improve the way they detect cyber threats, respond to incidents, and continuously monitor their systems and assets in real-time. Organizations and businesses need a more meaningful way to contain a breach rather than it being a notification that you already have an issue and it’s now moved into a cleanup operation.
4. Do we know how to respond to a cybersecurity emergency?
Incident Response (IR) is the managed approach an organization uses to prepare, detect, contain, and recover from a cyberattack. A cyberattack or data breach can be so damaging, potentially affecting customers, intellectual property, personally identifiable information (PPI), revenue, and ultimately reputation.
Having an incident response plan in place aims to reduce this damage and recover as quickly as possible. Additionally, organizations may discover that their insurance company will not accept their claim if they did not take certain predetermined steps. Immediately contact your insurance company and get direction from them at the very beginning of any IT remediation.
According to the National Institute of Standards and Technology (NIST), there are four key phases of Incident Response.
Steps of an Incident Response Plan
5. Do I need cybersecurity insurance?
The answer to this question is easy - YES.
Cyber liability insurance covers the cost for a business to recover from a data breach, virus, or other cyberattacks. It also covers legal claims resulting from the breach. Any business that stores sensitive data in the cloud or on an electronic device should have cyber liability insurance.
According to Sophos, cybersecurity insurance pays the ransom 94% of the time. Cybersecurity insurance is now the norm, with 84% of organizations reporting that they have it. However, only 64% of organizations have policies that cover ransomware incidents.
Even before the pandemic, cyber insurers were tightening their underwriting guidelines and asking for more details to better understand the risk they were insuring. Whether it is details on backup procedures or questions on specific security controls in place, companies looking for cyber insurance in 2021 can expect a more rigorous underwriting process.
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...

“When did this happen?”“About a year ago… well, thirteen months, actually.”

Artificial intelligence is everywhere, helping small businesses automate workflows, streamline processes, and boost productivity. But here’s the flip...