Endpoint Detection and Response (EDR): Enabling Secure Growth for Small Businesses
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

According to IBM’s 2021 Cost of a Data Breach Report, the healthcare industry suffered the highest average cost of a data breach for the 11th year in a row.
Practically every aspect of running a dental practice has gone digital, including digital radiography, scheduling, billing, charting, electronic health records, digital dentistry, and more. The amount of electronic protected health information (e-PHI) stored is increasing, and we’re seeing a rise in cyber-attacks targeting healthcare, including dental practices.
The healthcare industry is one of the most highly targeted for cybercrimes, given the confidential personally identifiable information (PII) contained in an electronic health record that is built to share information with other healthcare providers.
Also, the increased use of Internet of Things (IoT) medical devices like digital X-rays provides an easy entry point for attackers to hack into and exploit networks. The global Internet of Medical Things (IoMT) market is expected to surge to a $158 billion estimate in 2022, up from $41 billion in 2017.
The American Dental Association reported that in August 2019, hundreds of dental practices were affected by ransomware. The attack focused on a dental-focused technology provider, DDS Safe, which impacted approximately 432 dentists.
Today, dental cybersecurity attacks are on the rise. Cybercriminals are counting on dental offices having softer security policies in place or inadequate employee security guidelines and training compared to larger healthcare entities.
Hackers believe that many dental offices have an underinvestment in cybersecurity, both financially and in terms of employee security and training measures, knowing that it only takes one employee clicking on a bad link to make the entire network vulnerable. Cybercriminals also understand that dentists may have a large number of patient records.
Additionally, there are clear HIPAA compliance guidelines that medical practices, including dentists, orthodontists and more, must follow regarding protecting patient data. If your practice’s data gets breached, the agency’s Breach Notification Rule requires you to alert every patient of record that an incident has occurred.
Additionally, the financial penalties for HIPAA violations can be very costly to a practice, ranging from $100-$50,000 per PHI (Protected Health Information) record affected, with a maximum penalty of up to $1.5 million per year.
It’s time practices strengthened their security and the protection of their patient information. Here are some steps you can take to protect your practice.
1. Train Employees on Cybersecurity Awareness
Human error is still the number one cause of most data breaches in 2021. Researchers from Stanford University and a top cybersecurity organization found that approximately 88 percent of all data breaches are caused by an employee mistake.
Cybercriminals will take advantage of human error and vulnerabilities. One mistake from just one employee can put the security of your entire network at risk.
Rather than a one-time event, security awareness training is most useful when used as an ongoing practice in the framework of a bigger security awareness program. How to detect suspicious emails, social engineering tricks, phishing messages, etc.
Train your staff on various cybersecurity awareness topics, including:
2. Implement Advanced Security Features
There are several cybersecurity precautions that you can implement at the practice level to keep cybercriminals away, including:
Using strong passwords, longer, a combination of upper- and lower-case letters, numbers, and special characters.
Set a password policy that requires a new password every 3 months and has more than 13 characters.
Use Multi-factor Authentication to provide an added security measure that prompts a user for an additional form of identification upon sign-in such as a numerical code sent via text.
Adding advanced spam email filtering is a sophisticated email filter that uses AI to check every URL, attachment, images, and more to find advanced threats, vs. standard spam filters.
Software Patching: perform regular updates to ensure your software, dental devices, and web browsers are up to date.
Back up your data regularly. Backup solutions are of the utmost importance when ensuring data can be recovered, no matter the situation.
Advanced Endpoint Protection extends beyond antivirus guarding a corporate network by blocking access attempts and other malicious activities at their endpoints. Endpoint refers to any device on the network including desktop PCs, workstations, tablets, smartphones, servers, printers, and any other IoT devices that connect to the internet.
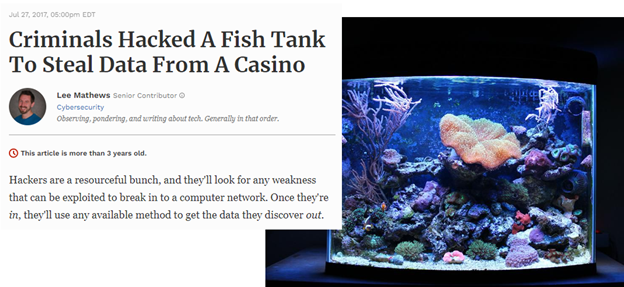 Hackers stole data from a Casino via the fish tank (endpoint) connected to their network.
Hackers stole data from a Casino via the fish tank (endpoint) connected to their network.
3. Create a formal Incident Response Plan
Incident Response (IR) is the managed approach an organization uses to prepare, detect, contain, and recover from a cyberattack.
A cyberattack or data breach can be so damaging, potentially affecting customers, intellectual property, personally identifiable information (PPI), revenue, and ultimately reputation. Having an incident response plan in place aims to reduce this damage and recover as quickly as possible. Responding quickly and appropriately to a cyberattack can significantly reduce the impact and cost of the incident.
4. Request a Professional Cybersecurity Risk Assessment
Conduct an audit of your security protocols by an outside Information Technology and Security team to ensure appropriate cybersecurity measures are in place, evaluated, reported, and provide necessary security remediation.
The cybersecurity vulnerability assessment should also include:
Planning: review local and cloud systems and networks for the location of sensitive information and critical systems.
Vulnerability scanning to identify security vulnerabilities in the practice’s procedures, computers/devices, and network.
Review and rank vulnerabilities, giving a clear sense of urgency and risk.
Working closely with your IT team and staff members to provide a remediation roadmap, identifying, and solving threats impacting your security and systems.
5. Cyber Insurance is a Must
The threat of a cyber-attack is too high, and the consequences can be devastating. At this point, it's important for all businesses to have cyber insurance regardless of their size, industry, or IT needs.
If your business stores or processes sensitive information like names, addresses, social security numbers, medical records, or credit card information you need cyber insurance.

Image courtesy of Travelers Insurance
If your dental practice experiences a data breach, your practice could experience legal consequences if patient information is compromised, and the costs to recover from a breach can be upwards of hundreds of thousands of dollars. Your patients could lose trust in your practice and seek dental care elsewhere.
Implementing the proper cybersecurity solutions can significantly reduce the potential risks and damages from a cyberattack on your practice.
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!
%20Enabling%20Secure%20Growth%20for%20Small%20Businesses.png)
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...