Endpoint Detection and Response (EDR): Enabling Secure Growth for Small Businesses
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...
3 min read
 Byron Martin
:
Jul 30, 2020
Byron Martin
:
Jul 30, 2020
It was one of those calls that I sometimes dread not knowing entirely what to expect.
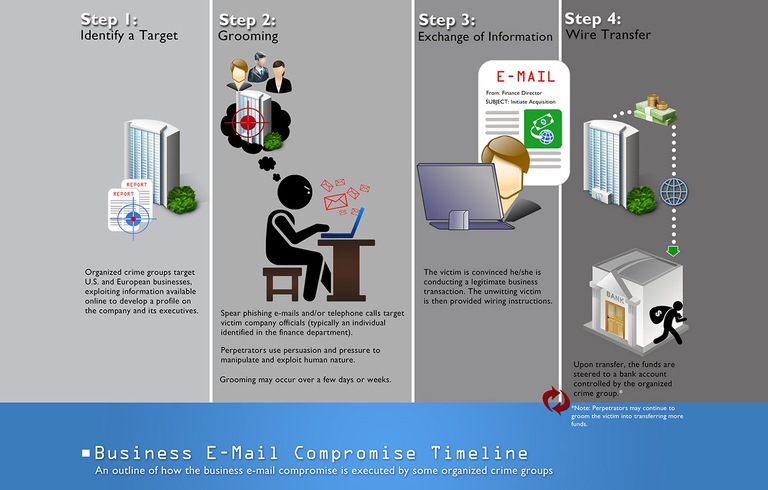
The caller was not a client, but it was a local small business that I was familiar with. They had discovered that someone may have... as they said "hacked" their email and as a result the hacker executed a strategic con that eventually resulted in the business electronically transferring over $150,000 dollars to the hacker. This type of breach is called a Business Email Compromise which is one of the most common cybercrimes that has now become a billion-dollar payday for cyber criminals.

Business Email Compromise Cost - Image Source Darkreading.com
I don't fault anyone for falling prey to these schemes as the bad guys have gotten extremely cunning and skilled at pulling off this kind of theft. The criminal organizations even employ lawyers, linguists, hackers and social engineers in order to pull off many forms of modern-day cons and deception. These are not small groups but are large business enterprises employing thousands. This is a global multifaceted problem working at many levels of sophistication and is a serious threat that continues to escalate year over year.
Cybercriminal Tactics:
There are a handful of ways cyber criminals get their foot in the door, I will focus on the two that I see happen most frequently.
First: Email Phishing or Spear Phishing. All it takes is a quick look at LinkedIn or other social media to find out about the CEO, the Bookkeeper or any other role that has the potential to move money. Once they have identified those individuals, they will begin their campaign of Spear Phishing emails and telephone calls. They will repeatedly target those individuals and as they gather more intel, they get better at specifically targeting you. Their aim is to have you reveal enough information that they can then manipulate you into interacting with them or simply click on an email that has malware imbedded in it. Once the malware has executed it can gather information such as passwords, personal information, or even full access to your email.
Second: This method is common and unfortunately often overlooked. It is hard to manage unique passwords for everything, the pitfall then resulting in people reusing passwords for multiple systems and websites. How often are your employee network passwords the same ones they use online for personal email or online shopping? We read regularly of hacked online credentials for anything from Facebook to Marriot Hotel. If I am a hacker and I can do a quick search on the Dark Web for credentials used by Byron Martin... It just costs me a few bucks to purchase those credentials which I can then to log into Byron's company email or company computer systems. No Hacking Required!
Image source courtesy of the FBI
You've been Breached!
Once they gain access, they can have full visibility of company email access to email threads with information such as invoices, client names, vendors or even pending wire transfers.
What is scary in the case I mentioned at the beginning is that the bad actors had been in their system for weeks if not months. Reading emails, learning more about the client, the projects they had going on, who their clients were etc. Then when they had learned all they needed to know, they intercepted emails, changed key financial information around wire and ACH transfers during which time the business they had no idea that this information was being manipulated until it was too late.
How do you Combat these Threats?
Sometimes the insignificant things that can make a substantial difference and it does not have to break the bank. Unfortunately, many small businesses do not know about the threats or how some simple and affordable measures can save them from severe financial and emotional burdens. Here are a few pre-emptive measures that any business can and should take.
All is not lost, we can Help!
If you feel like you could use a little guidance on getting things started with any of the above preemptive measures, we'd happily chat and make recommendations and no cost to you. These can be simple to implement, can be 'al la carte' and don't require service contracts.
![]() Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
Teknologize is a SOC 2 Type II accredited Managed IT and Cybersecurity provider serving small to mid-sized businesses across Washington and Oregon. We deliver full-service Managed IT Support, Co-Managed IT Support, advanced Cybersecurity Solutions, and IT Compliance Services for regulated industries, including Healthcare, Financial Institutions, the Utilities Sector, Manufacturing, and Professional Services.
👉 Book a Discovery Call to see how Teknologize can support your business.
Our Offices
Tri-Cities, Washington – 509.396.6640 | Yakima, Washington – 509.396.6640
Bend, Oregon – 541.848.6072 | Seattle, Washington – 206.743.0981
Questions about your IT or Cybersecurity? Give us a call today!
Watch the full Podcast on what is a Business Email Compromise (BEC) and how cybercriminals execute the modern-day con.
%20Enabling%20Secure%20Growth%20for%20Small%20Businesses.png)
Cybercriminals don’t go after businesses because they’re big.They go after businesses because they’re accessible. According to the IBM Cost of a...

IT Support Companies Can All Sound the Same, Until You Know What to Look For Business owners all want the same thing from their IT: reliability,...

Many SMBs don’t actually have an IT budget; they have a list of last year’s expenses. Everything goes into one bucket, and next year’s “budget” is...